Android Data Recovery
Recovery-Android Products Center

WINDOWS
MAC
We live in a world where data hacks and private information leaks are becoming common. The continuous increase in smartphone use also means that cyber-criminals target smartphones specifically. If you are looking for ways on how to keep your Android phone safe from hackers, you’ve come to the right ...
Read More >>
Cybersecurity And The Android Platform These days, we live in the era of cybersecurity risks. What does this mean? Well, the term cybersecurity refers to general safety online -a.k.a cyberspace. It has become really important to pay attention to the 'security' of your mobile device, especially s...
Read More >>VPS hosting is a powerful tool for websites that need reliability, and control. However, you never know when changes need to be made – management on the go may have already crossed your mind. So, how can you manage your VPS from an android device? But before delving into that, make sure you have a r...
Read More >>Group chat apps are a must-have communication tool for businesses, especially startups. They provide affordable ways to create a hub of partnerships, collaborations, and teams. Considering the physical restrictions we all now face due to COVID_19, chat apps offer a solution. These apps enable virtua...
Read More >>The portability and rapid advancement in the field of technology have forced masses to heavily rely on these products. The increased functionalities of our smartphones, laptops, and other smart devices have made our life a lot easier. Now we can browse through social media, listen to our favorite mu...
Read More >>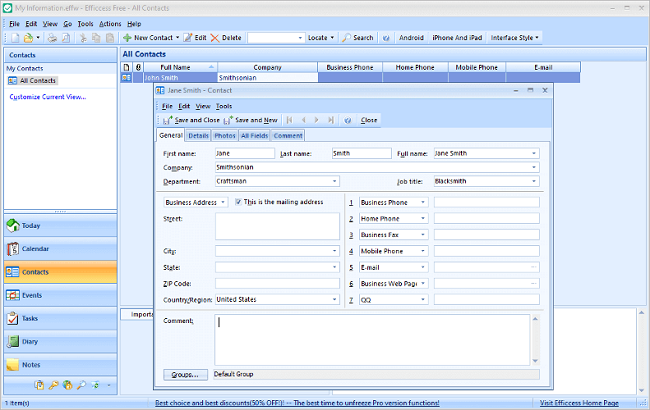
At first, it is easy to handle the address book, but it soon becomes a complicated operation. When the contact list expands, identifying contacts in time, using the information for marketing campaigns, and verifying whether the data is still accurate, becomes nearly impossible. The reasons for not h...
Read More >>Mobile app market significantly contributes in raising the world digital economy. The convenient lifestyle in a fast paced world offered by mobile apps is the major reason behind its popularity. To meet the exponential demands and expectations of the mobile app users businesses across the globe are...
Read More >>
Becoming an Android developer in 2020 is both ambitious and challenging. While it is a career with never-ending job prospects, getting to the point where you are a good Android developer takes quite a lot of time and effort. That’s why you need to know some tips and tricks that will help you reach...
Read More >>The cycle of innovation, which started from a wheel, has come a long way as humans have conquered the skies with airplanes and dominated the land with advancements like cars and motorbikes. Likewise, the communication sector has made great strides since the invention of the phone. Gradually, with th...
Read More >>
Can a regular TV become something akin to a PC? Yes, it can, all you need is an IPTV set-top box connected to it. Browsing the web, streaming content, and playing online games—all that brought to your TV with a tiny little box. And the best ones you can find are the set-top boxes running Android TV...
Read More >>
IT Professionals are constantly looking for the best ways to securely transfer enterprise files and applications. When handling sensitive business data, secure transfer methods are essential to protect your documents. Luckily, there are several transfer strategies and methods to m...
Read More >>In 2018 alone, consumers purchased roughly 1.3 billion Android smartphones. Worldwide Android dominates nearly 90% of the market through extremely popular brands like Samsung, Huawei, OPPO, and many others. There’s plenty to love about Android—it’s versatile, simple, and highly customizable. With su...
Read More >>
In the digital age it is vital for businesses to have a website. It is mostly common knowledge that having an attractive, organized, up to date site layout can help attract consumers. What can be easily overlooked is the importance of loading time. Consumers want instant gratification, if your page ...
Read More >>Finding love has never been easier thanks to online dating, some would say. What are the perfect ingredients for finding the love of your life? Well, just a smartphone will do. In recent years, dating apps have been the frontrunners in the matchmaking process. Many have found love by using these app...
Read More >>
Smartwatches almost seem like something of the future. They are essentially a smartphone that you can wear around your wrist and offer many convenient features. If you are interested in smartwatches or considering purchasing one, read on to learn more. A Brief History of Smartwatches Digital w...
Read More >>
It’s not a rare occurrence for inboxes to be filled with spam, but when the emails received are threatening, action should be taken. Fortunately, long gone are the days where these senders could get away with it. Today, there are tools like reverse email lookups that expose the people responsible. Y...
Read More >>
RecoveryAndroid is a renowned website dedicated to gleaning and offering expert solutions and feasible tricks to Android users, which has been helping out millions of users for now. However, as you can easily tell from its name, RecoveryAndroid is the expert in the field of Android things. In terms ...
Read More >>
Like any flawlessly functional piece of software, it's easy to overlook the work done by the software developers and programmers of the best mobile casino games out there. It's really only when the programs go seriously wrong that the poor programmers are noticed for their role in bringing the soft...
Read More >>
So, you have the world's best idea for a new app? You are 100% convinced that this will be the next Facebook, Uber or Instagram. It is important to know that there are some questions to ask when trying to build the perfect app. These questions have to have very clear answers before even writing the ...
Read More >>
We can easily find millions of apps in Google Play Store today. Thanks for the development of technology, we can find apps that can cater to our every need. As the proverb goes, Apps are the beating heart of Android. Thinking about installing apps on your phone? Learn more about these five useful An...
Read More >>
The question what is better iPhone or Android smartphones is a very important for those who is going to buy a new device. Nowadays users try to find out which platform is better iOS or Android. Some years ago such choice had no sense because for people everything was rather clear: if you want to buy...
Read More >>
By virtue of its ability and being the gadget closest to you most of the time, your phone becomes one of the gadget that carries some of your most important data. From music files to work documents and class work, the phone has virtually become a personal computer. Thus you can imagine the amount o...
Read More >>Games are the best part of smartphones. Ever since snake started appearing on old Nokias, gaming and phones have just gone together. In today's modern market, you might have a great time with gambling apps, for example - there's nothing like playing a quick hand of poker and then going out and buyin...
Read More >>
Facebook is one of the most essential apps that you can use on your Android phone. Whether you would like to reconnect with friends, spend time chatting or even if you want to just download pictures from your account to your phone, Facebook can do a lot. Connecting with your friends as well as insta...
Read More >>